Bybit hack, $1.4 billion in ETH
The Bybit Exchange Hack of February 2025: A Comprehensive Analysis
In February 2025, cryptocurrency exchange Bybit suffered what has become the largest digital heist in cryptocurrency history, with losses totaling approximately $1.5 billion. This sophisticated attack, attributed to North Korean state actors, exposed critical vulnerabilities in multi-signature wallet systems and highlighted the evolving nature of threats in the cryptocurrency space. The incident involved a complex chain of events including the compromise of a developer’s machine, manipulation of transaction interfaces, and rapid laundering of stolen funds.

Timeline of the Bybit Security Breach
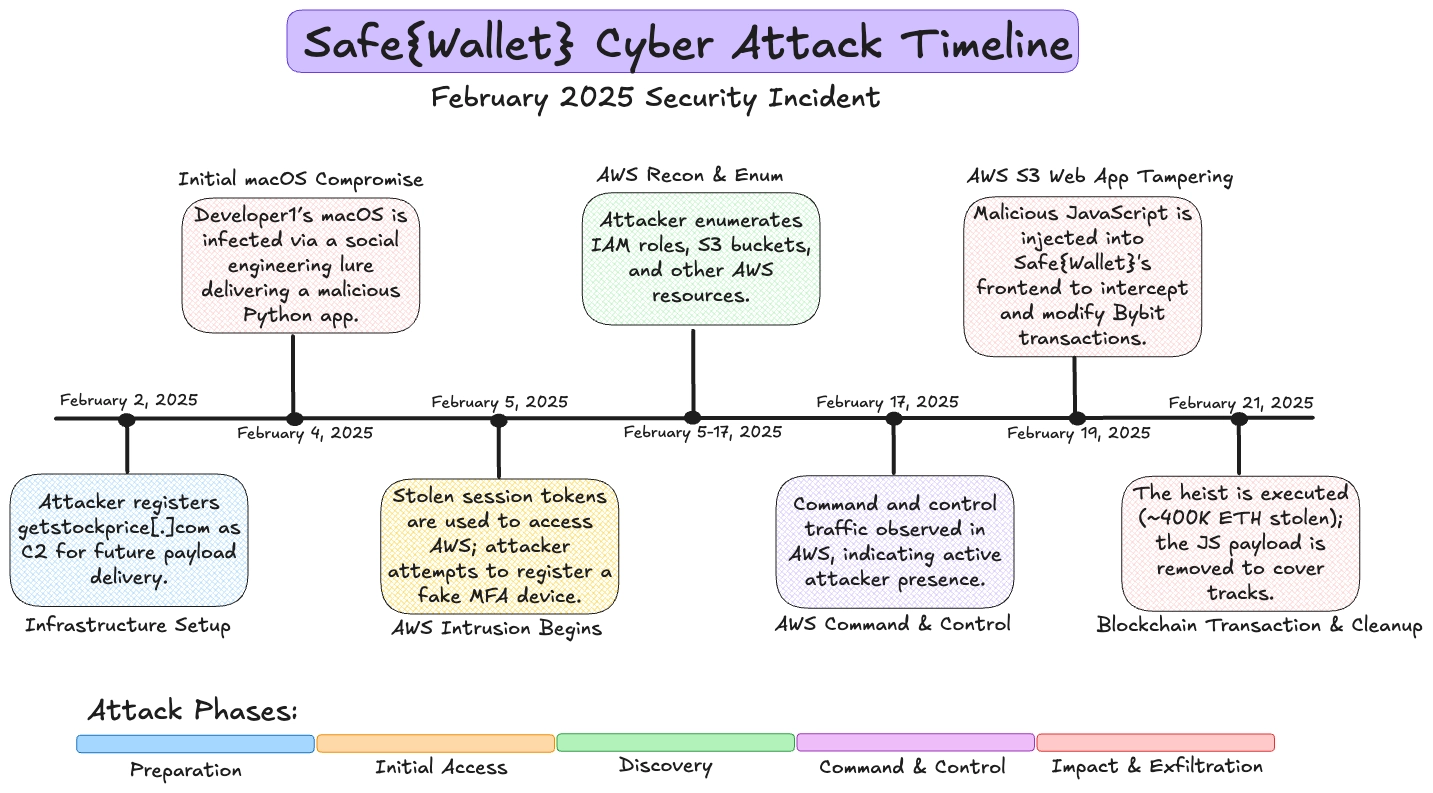
The February 2025 Bybit hack was meticulously planned and executed with precision. According to forensic analysis conducted by Mandiant, the North Korean-affiliated hackers spent 19 days preparing for the attack before its execution. The actual breach began on February 21, 2025, at approximately 14:15 UTC, when attackers initiated a small test transaction of 90 USDT from Bybit to their controlled address. This initial transaction served as a verification that their system compromise was successful and operational.
Just one minute later, at 14:16 UTC, the attackers executed the main attack, withdrawing an enormous amount of cryptocurrency: 401,347 ETH, 90,375 stETH, 15,000 cmETH, and 8,000 mETH, with a combined value of approximately $1.4-1.5 billion. The timing of the attack appears deliberate, occurring on a Friday late in the day for many regions, including Bybit’s headquarters in Dubai, when staffing would likely be reduced and response capabilities limited.
By 14:29 UTC, merely 14 minutes after the major withdrawal, the attackers had already begun laundering the stolen funds. They initiated this phase with a test transaction of 1 ETH to a new address, then proceeded to rapidly exchange the various tokens (stETH, cmETH, and mETH) for Ethereum using decentralized finance services in batches of approximately 10,000 tokens. This laundering operation was conducted simultaneously across multiple addresses, demonstrating a high level of organization and possibly automated processes designed to quickly obscure the movement of stolen assets.
The first public confirmation of the incident came from Bybit approximately an hour and a half after the attack began, with an announcement posted to their X (formerly Twitter) account at around 15:51 UTC[1]. By March 4, 2025, Bybit CEO Ben Zhou reported that while about 77% of the funds (valued at roughly $1.07 billion) remained traceable on-chain, approximately $280 million had already “gone dark”. More alarmingly, reports indicated that by March 6, the hackers had managed to launder 100% of the stolen cryptocurrency in just 10 days.
 source: https://www.elastic.co/security-labs/bit-bybit
source: https://www.elastic.co/security-labs/bit-bybit
Attack Mechanism and Compromised Systems
The Bybit hack represents a sophisticated operational security breach rather than a traditional smart contract exploit. The attack originated not within Bybit’s own infrastructure but through a compromise of Safe{Wallet} (formerly known as SafeWallet), the multi-signature wallet platform used by Bybit for managing its cold storage.
Forensic investigations by security firms Sygnia and Verichains revealed that the attackers first compromised a Safe{Wallet} developer’s MacOS system, likely through malware installation. Through this initial access, they were able to hijack the developer’s Amazon Web Services (AWS) session tokens, effectively bypassing the multifactor authentication security measures implemented by Safe{Wallet}. Notably, Safe{Wallet}’s AWS settings required team members to reauthenticate their session tokens every 12 hours, which prompted the hacking group to attempt registration of an MFA device to maintain persistent access.
With access to the AWS environment, the attackers injected malicious JavaScript code into app.safe.global, the web application used by cryptocurrency exchanges like Bybit to manage their multi-signature wallets. This malicious code was specifically designed to activate only under certain conditions, ensuring that regular users would not detect the backdoor while high-value targets like Bybit would be compromised. The selective triggering mechanism demonstrates the highly targeted nature of this attack.
The most insidious aspect of the attack involved manipulating the user interface presented to Bybit’s operators. During what appeared to be a routine transfer of ETH from Bybit’s multi-signature cold wallet to its hot wallet, the attackers altered what the operators saw in the Safe{Wallet} interface. The transaction details displayed to the operators did not reflect the true, malicious nature of the transaction being signed. When Bybit staff approved what they believed was a legitimate transfer, they unwittingly granted the attackers control over the cold wallet by replacing Bybit’s vault keys with those controlled by the attackers.
Attribution and Tactics of the Threat Actors
Multiple security firms and government agencies have attributed this attack to North Korean state-sponsored hackers, specifically the notorious Lazarus Group. This attribution is based on several factors, including Mandiant’s forensic analysis, which confirmed the hackers were North Korean state actors who took 19 days to prepare and execute the attack[6]. The FBI also published an alert specifically identifying the attackers as North Korean hackers and asking node operators to block transactions from wallet addresses linked to them.
The attack methodology bears significant similarities to previous operations attributed to the Lazarus Group. Similar techniques were employed in attacks against other cryptocurrency platforms including WazirX and Radiant Capital, where attackers also exploited weaknesses in multi-signature systems by manipulating transaction data. This pattern suggests a refinement of tactics by this threat actor, moving from direct smart contract exploits to more sophisticated operational security breaches targeting the human and infrastructure elements of cryptocurrency platforms.
The sophistication of the laundering operation following the theft further supports the attribution to a well-organized state-sponsored group. The attackers demonstrated the capability to rapidly distribute and convert large amounts of cryptocurrency across multiple accounts in parallel, suggesting significant resources and possibly automated tools designed specifically for this purpose. This ability to quickly obscure the trail of stolen funds is consistent with previous operations attributed to North Korean hackers.
SafeWallet’s Post-Mortem Findings
According to a post-mortem report released by SafeWallet, developed in collaboration with Mandiant, the attack involved several sophisticated steps to bypass security measures. After compromising the developer’s MacOS system, the attackers made several failed attempts at registering a multifactor authentication device before successfully using the AWS session tokens obtained from the compromised system. Once inside the AWS environment, they worked methodically to set up the attack infrastructure.
Remarkably, the attackers demonstrated operational security awareness by cleaning up evidence of their intrusion. According to Sygnia’s analysis, “Two minutes after the malicious transaction was executed and published, new versions of the JavaScript resources were uploaded to Safe{Wallet}’s AWS S3 bucket. These updated versions had the malicious code removed”. This rapid cleanup effort indicates a desire to limit detection and forensic analysis of their methods.
Mitigation Measures and Industry Response
In the aftermath of the Bybit hack, several mitigation measures and industry responses have been implemented. Safe{Wallet} has put additional safeguards in place, though they emphasized that the cybersecurity exploit did not affect their smart contracts themselves, which remained secure throughout the incident. This distinction highlights the importance of securing not only the blockchain technology itself but also the supporting infrastructure and human elements that interact with it.
The FBI took the unusual step of publishing an online alert asking node operators to block transactions from wallet addresses linked to the North Korean hackers, warning that the stolen funds would be laundered and converted to fiat currency. Despite these efforts, the attackers successfully laundered 100% of the stolen cryptocurrency in just 10 days, demonstrating the challenges faced by law enforcement in responding to such incidents in the fast-moving cryptocurrency ecosystem.
Bybit has launched a recovery bounty program, offering up to 10% of the recovered amount to individuals who assist in retrieving the stolen cryptocurrency. They are also actively collaborating with industry experts, including blockchain analytics firm Chainalysis, to trace and potentially recover the stolen assets. As of March 4, 2025, Bybit CEO Ben Zhou reported that approximately 77% of the funds, valued at roughly $1.07 billion, remained traceable on-chain, offering some hope for potential recovery.
The cybersecurity firm Trail of Bits has emphasized that this attack could potentially have been prevented through comprehensive threat modeling, which would have identified the operational security vulnerabilities before they could be exploited. They noted that while traditional code audits focus on finding implementation bugs in smart contracts, only threat modeling can reveal the systemic and operational weaknesses that enabled this particular breach.
The SafeWallet team has called for continued improvements to user experience and user interfaces to combat similar future threats. This recommendation acknowledges that even with technically secure systems, the human-computer interface remains a critical vulnerability that attackers can exploit through social engineering and interface manipulation.
Broader Implications and Lessons Learned
The Bybit hack represents a significant evolution in the threat landscape facing cryptocurrency exchanges and platforms. Unlike earlier cryptocurrency heists that primarily exploited flaws in smart contract code, this attack targeted the operational and human elements of the system, using sophisticated social engineering and interface manipulation to trick authorized users into approving malicious transactions.
This incident highlights several critical vulnerabilities in current cryptocurrency security practices. First, it demonstrates that multi-signature wallet solutions, while theoretically more secure than single-signature alternatives, can still be compromised if the interfaces used to interact with them are manipulated. The attackers did not need to break the cryptographic security of the blockchain itself; they simply needed to trick human operators into approving a transaction whose true nature was hidden from them.
Second, the attack underscores the importance of securing the entire technology stack involved in cryptocurrency operations, not just the blockchain and smart contract components. In this case, the vulnerability originated in the AWS infrastructure supporting the Safe{Wallet} application, highlighting how cloud security practices directly impact cryptocurrency security. The compromise of a developer’s workstation and subsequent theft of AWS session tokens provided the initial access that made the entire attack possible.
Third, the incident demonstrates the increasing sophistication of state-sponsored threat actors in the cryptocurrency space. North Korean hackers have a well-documented history of targeting cryptocurrency platforms, but this attack shows an evolution in their tactics from direct technical exploits to more complex operational security breaches. This trend suggests that cryptocurrency platforms must evolve their security practices accordingly, with increased focus on securing the human elements of their operations and implementing robust threat modeling practices.
Conclusion
The February 2025 Bybit hack stands as the largest cryptocurrency theft in history, resulting in the loss of approximately $1.5 billion in various Ethereum-based tokens. Attributed to North Korean state-sponsored hackers from the Lazarus Group, the attack exploited vulnerabilities in the operational security of Safe{Wallet}, the multi-signature wallet platform used by Bybit, rather than flaws in blockchain technology itself.
The attack methodology involved compromising a developer’s workstation, stealing AWS session tokens, injecting malicious JavaScript into the Safe{Wallet} web application, and manipulating the user interface to trick Bybit operators into authorizing a transaction that granted attackers control of the exchange’s cold wallet. The sophisticated nature of the attack, including targeted payload delivery and rapid laundering of stolen funds, demonstrates the evolving capabilities of state-sponsored threat actors in the cryptocurrency space.
Industry response has included enhanced security measures by Safe{Wallet}, collaboration with blockchain analytics firms to trace stolen funds, and calls for more comprehensive threat modeling to identify and mitigate operational security vulnerabilities. The incident highlights the critical importance of securing not only the technical components of cryptocurrency systems but also the human and operational elements that interact with them. As cryptocurrency platforms continue to hold increasing amounts of value, the security practices protecting these assets must evolve to address the sophisticated threats posed by well-resourced and persistent adversaries.