ZKsync Security Breach
ZKsync Security Breach: Analysis of the $5 Million Token Theft
On April 15, 2025, ZKsync, a prominent Ethereum layer-2 scaling solution, suffered a significant security breach when hackers compromised an administrative wallet and minted unauthorized tokens worth approximately $5 million. The incident specifically targeted unclaimed airdrop tokens, resulting in market volatility and raising questions about security practices within the protocol. This report examines the breach details, ZKsync’s response, market impact, and broader security implications for the cryptocurrency ecosystem.
The Attack Vector and Compromise Details
Administrative Wallet Exploitation
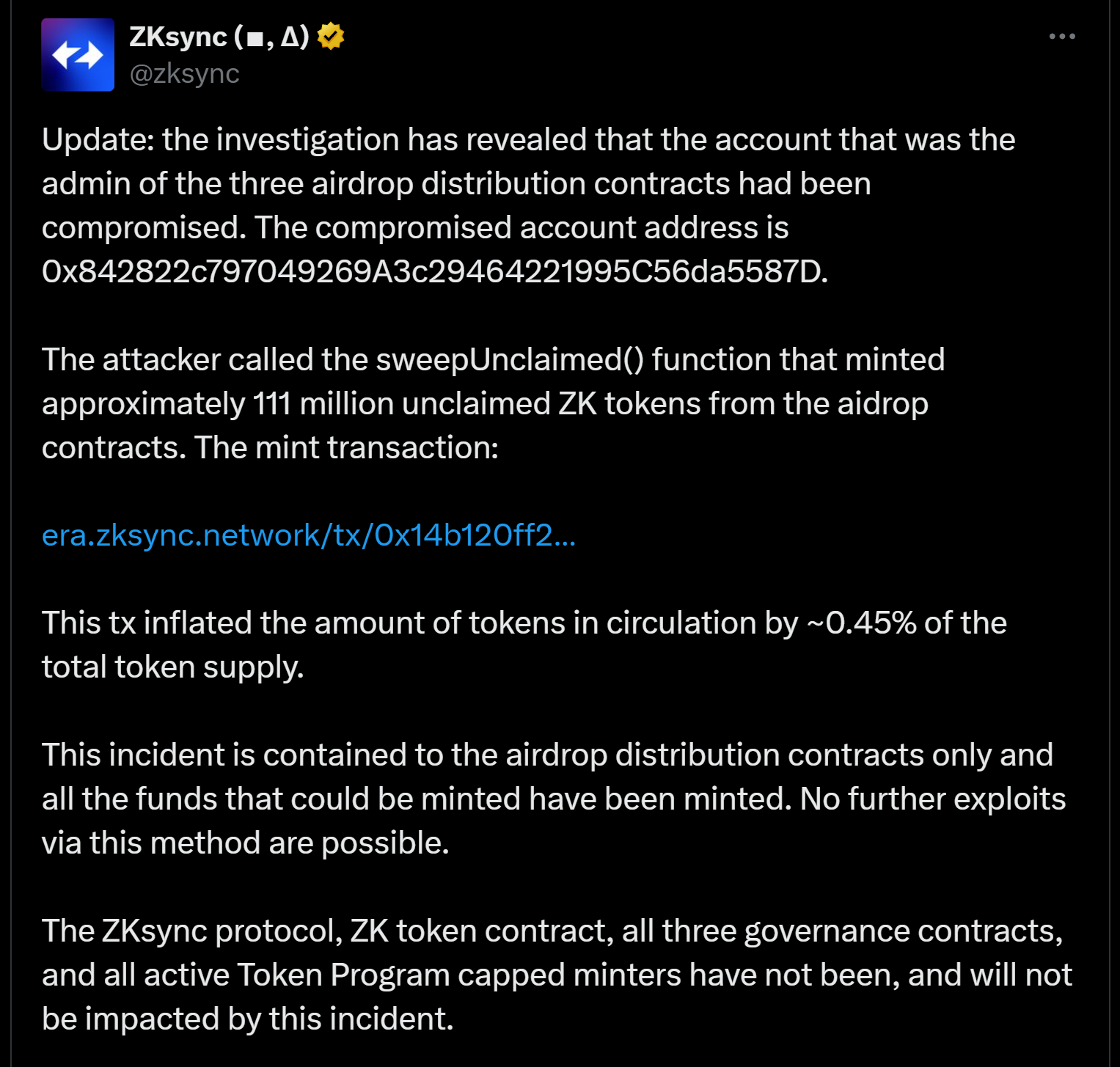
The security breach centered on a compromised administrative account that had control over three airdrop distribution contracts. ZKsync identified the affected admin wallet address as 0x842822c797049269A3c29464221995C56da5587D in their official statement. The attacker leveraged this access to exploit a specific contract function designed to handle unclaimed tokens from the project’s recent airdrop campaign. Here we can see the updates from their side:
Technical Exploitation Mechanism
The attacker specifically targeted the airdrop distribution mechanism by calling the “sweepUnclaimed()” function within the compromised contracts. This function allowed the unauthorized minting of approximately 111 million unclaimed ZK tokens that had been reserved for users who had not yet claimed their airdrop allocation. By exploiting this administrative function, the attacker was able to mint these tokens and gain control over assets that represented a significant portion of the unclaimed airdrop supply.
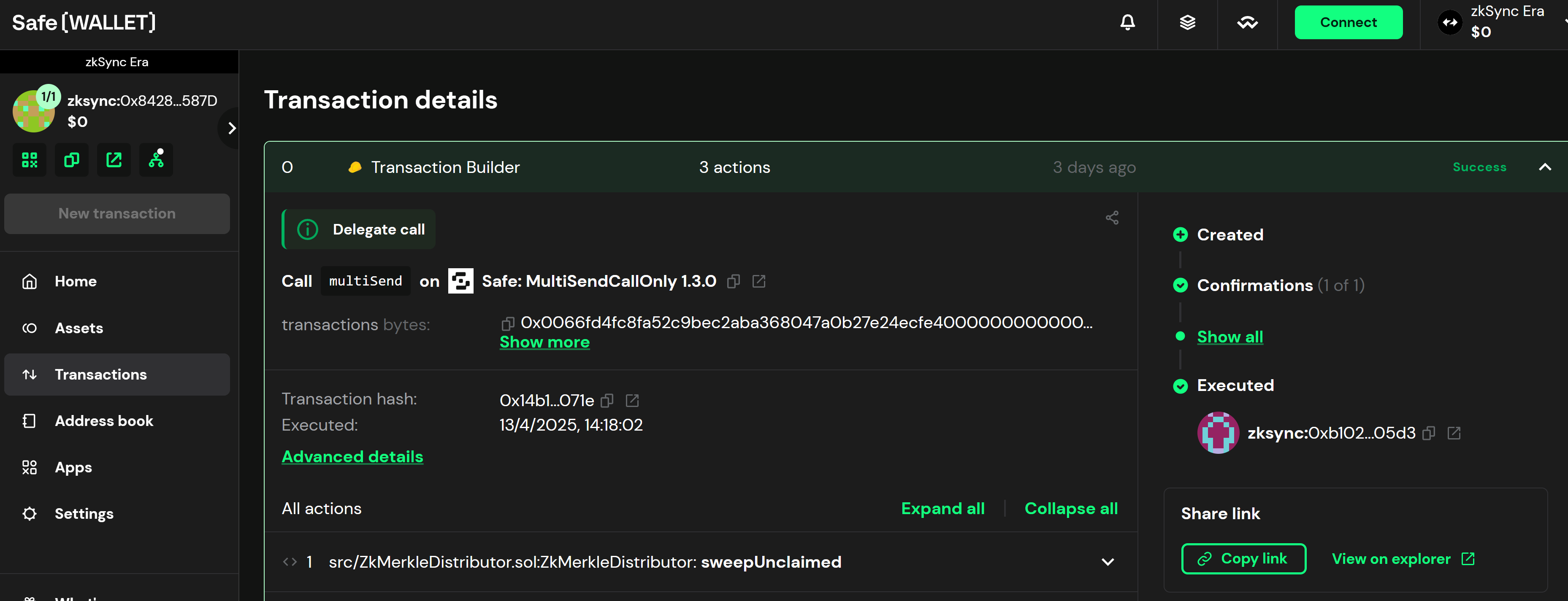
Another technical detail is that the transactions from the compromised Safe wallet were configured for only 1 validator for the tx. It is highly recommended to have more than 1 validators per transaction. This is a best practice to ensure the security of the transaction and prevent any potential exploits.
Scope and Scale of the Breach
The security team at ZKsync quickly determined that the attack was isolated to the airdrop distribution contracts only. The scope of the breach resulted in the unauthorized minting of tokens that increased the total token supply by approximately 0.45%. This relatively contained percentage suggests that while significant, the breach did not fundamentally alter the token’s overall economics. Most of the stolen tokens reportedly remain in a wallet controlled by the attacker (0xb1027ed67f89c9f588e097f70807163fec1005d3).
ZKsync’s Response and Remediation Efforts
Immediate Containment Actions
Upon discovering the breach, ZKsync moved swiftly to contain the situation and provide transparency to its users. The team released an official statement confirming that “this incident is contained to the airdrop distribution contracts only, and all the funds that could be minted have been minted. No further exploits via this method are possible”. This clarification was crucial in preventing market panic by establishing the limited scope of the vulnerability.
Infrastructure Security Assessment
ZKsync conducted a thorough investigation to determine the extent of the compromise and explicitly confirmed that core protocol components remained secure. According to their statement, “The ZKsync protocol, ZK token contract, all three governance contracts, and all active Token Program capped minters have not been, and will not be impacted by this incident”. This clarification was essential in reassuring users that their personal funds and the broader protocol infrastructure remained unaffected.
Recovery Coordination Efforts
The team has initiated coordination with security firm Seal 911 (SEAL) and major cryptocurrency exchanges to assist in recovery efforts. As part of their response strategy, ZKsync directly addressed the attacker, encouraging them to “get in touch with security@zksync.io to negotiate the return of the funds and avoid legal liability”. This approach reflects standard practice in the cryptocurrency industry, where teams sometimes attempt to negotiate with attackers to recover stolen assets.
Market and Community Impact
Token Price Volatility
The news of the security breach immediately impacted the ZK token’s market performance. Following the announcement, the ZK token price experienced a significant drop of approximately 10-19% according to various sources. By the end of the trading day, the price had recovered somewhat, closing with a 5% loss. As of April 16, 2025, the token was trading at around $0.047, showing signs of recovery from the initial shock.
Trading Volume Response
While the price fell, trading activity increased substantially, with 24-hour volume rising by 96% to $71 million according to data reported by CoinDesk. This surge in trading volume demonstrates the market’s immediate reaction to the security incident, as both sellers responding to the negative news and opportunistic buyers entered the market.
Community Trust Concerns
The breach has generated significant frustration within the ZKsync community, with many users expressing concerns about the project’s security practices and transparency. Community members have questioned how such a critical access point could be compromised in a project of ZKsync’s scale and reputation. Some users have drawn connections between this incident and broader concerns about token distribution mechanisms, with one community member commenting, “The same tokens you couldn’t give the community… A good way to exit, though”.
Broader Security Implications for Crypto
2025 Crypto Security Landscape
This incident contributes to a troubling trend in cryptocurrency security for 2025. According to reports, total losses from cryptocurrency-related hacks and thefts have already surpassed $1.77 billion in just the first quarter of the year. The ZKsync breach, while significant, represents only a portion of this larger security challenge facing the industry.
Centralization Risks in Decentralized Systems
The breach highlights a fundamental tension in supposedly decentralized systems: the presence of centralized points of failure. Despite ZKsync’s focus on decentralization through its layer-2 scaling technology, the compromise of a single administrative account led to significant financial consequences. This raises important questions about key management practices and access controls within decentralized finance (DeFi) projects.
Airdrop Security Vulnerabilities
The specific targeting of unclaimed airdrop tokens exposes potential vulnerabilities in token distribution mechanisms. As airdrops have become a popular method for distributing tokens and building community engagement, this incident serves as a reminder that these distribution methods can introduce unique security challenges if not implemented with robust protective measures. The exploitation of the “sweepUnclaimed()” function specifically demonstrates how administrative capabilities designed for legitimate purposes can become attack vectors when access controls fail.
Technical Context of ZKsync
Layer-2 Scaling Technology
ZKsync operates as an Ethereum layer-2 scaling solution that utilizes zero-knowledge proofs to process transactions more efficiently than the Ethereum mainnet. This technology allows for faster transaction processing and lower fees while maintaining security guarantees through cryptographic proofs that verify the validity of transactions without revealing their contents.
Protocol Infrastructure and TVL
Prior to the breach, ZKsync maintained a significant position in the layer-2 ecosystem with over $500 million in total value locked (TVL) according to some reports, while other sources cite a more conservative figure of $57.3 million TVL as of April 15, 2025. Regardless of the exact figure, ZKsync represents an important infrastructure component in the Ethereum scaling ecosystem.
Airdrop Context
The compromised tokens were part of ZKsync’s recent airdrop initiative, which was distributing 17.5% of its token supply to ecosystem participants. Airdrops have become a standard method for protocols to distribute governance tokens to users and build community engagement, but this incident raises important questions about the security of such distribution mechanisms.
Conclusion
The ZKsync security breach of April 15, 2025, while contained to airdrop distribution contracts, represents a significant incident in the cryptocurrency security landscape. The compromise of an administrative wallet leading to the unauthorized minting of 111 million ZK tokens worth $5 million highlights vulnerabilities that can exist even in sophisticated blockchain protocols.
ZKsync’s response has emphasized the isolated nature of the breach and the continued security of core protocol components and user funds. Nevertheless, the incident has impacted market confidence, as evidenced by the token’s price volatility, and raised important questions about security practices, administrative access controls, and the centralization of supposedly decentralized systems.
As ZKsync works with security partners to potentially recover the stolen funds, this incident serves as a reminder of the ongoing security challenges facing the cryptocurrency industry in 2025. For projects implementing token distribution mechanisms like airdrops, the breach underscores the importance of robust security measures around administrative functions and access controls to prevent similar exploits in the future.